Microsoft OneNote is a popular note-taking application that allows users to store and organize their notes across multiple devices. Here at Infosec Insights, we love this program to create notes and keep ourselves organized. Recently a new vector of attack has been discovered in OneNote. OneNote files can be used as a vector for malware to infect a Windows device. Fortunately, there are steps that businesses can take to prevent this from happening.
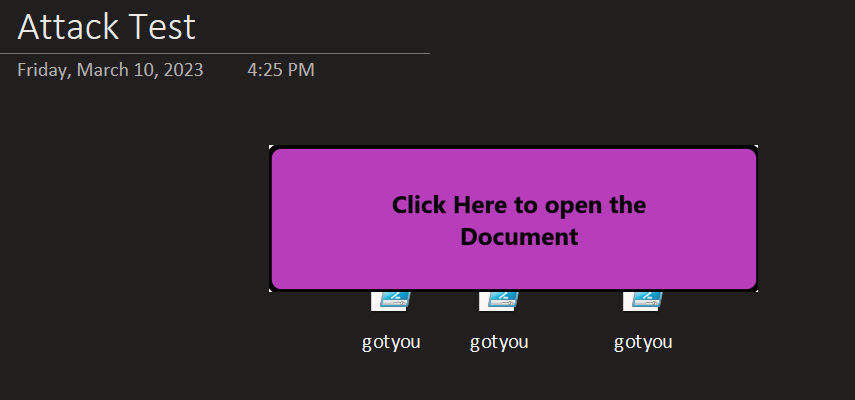
The most recently discovered attack in which OneNote files can be used to infect a Windows device is through the use of embedded objects. What an attacker is doing is sending a OneNote (.one) file to unsuspecting victims. This is bypassing a lot of email filters upfront since it is not a file type email filters are scanning for. The victim clicks the embedded object which doesn’t pop up with a security warning or anything that would alert a user that they are doing something that they maybe shouldn’t. An embedded object is a file that is attached to a OneNote note and is displayed within the note itself. This can include files such as vbs scrips, PowerShell files, or even executable files.
Here are some tips:
- Use email filters: Administrators can set up filters that automatically redirect messages with suspicious attachments or links to a separate folder or delete them altogether. To mitigate this attack, consider filtering out file type .one if your business does not have the need to use this file type.
- Educate your users: The human element is usually the weakest part of cybersecurity. If you do have a business need to accept OneNote files, educate your employees! Attackers keep trying new methods and all it takes is one wrong click. The more you teach your users, the less likely they are to click something harmful.
- Limit access to OneNote: Admins should consider limiting access to OneNote if their users don’t have a need to use it. Allowlisting is a powerful tool is used correctly. If your business doesn’t have the capability, you should consider obtaining it.
- Stay up to date: Users should regularly update their OneNote application and operating system to ensure that they have the latest security patches and bug fixes.
By following these tips, users can help protect their OneNote account from email-based cyberattacks and filter out harmful file types in emails. While there is no foolproof way to prevent all attacks, taking these steps can significantly reduce the risk of malware infecting a user’s notes and devices.
As always, it’s also important to keep OneNote and the Windows operating system up to date. Microsoft regularly releases security updates and patches for both OneNote and Windows that address known vulnerabilities. Administrators should make sure that they have the latest updates installed and have a systematic way of rolling out patches to prevent malware from exploiting known vulnerabilities.
In conclusion, while OneNote is a powerful and convenient note-taking application, it is not immune to security vulnerabilities. By taking these steps, users can help protect their devices and data from cyber threats. If you would like to know additional details about this attack type, and other mitigation methods with steps to follow, please visit this wonderful writeup on Bleeping Computer: www.bleepingcomputer.com/news/security/how-to-prevent-microsoft-onenote-files-from-infecting-windows-with-malware/